Configure KOTS to save tenant assets in Amazon EFS
When you configure KOTS to save tenant assets in Amazon EFS, the tenant assets are saved if a cluster fails. EFS provides automatic backups of the tenant assets and EFS is automatically scaled as you add and remove assets.
Important
Complete this task before Jama Connect is deployed. Otherwise, if you want to move your assets to EFS, you must first back up tenant assets to a TAR in KOTS.
Requirements
A KOTS cluster must be up and running.
You must be able to create and modify these AWS resources: IAM roles, IAM policies, security groups, EC2 instances, and EFS file systems.
The cluster must have internet access to download the EFS driver and associated containerd images.
Ports 9909 and 9809 must be available for the EFS driver to function successfully.
Create a new EFS dedicated to your KOTS stack because each Persistent Volume requires an EFS point, and access points are limited. Currently, each EFS can have a maximum of 120 access points. A dedicated EFS allows you to future-proof the cluster. The steps are provided below.
Note
Make sure you copy the Amazon Resource Names (ARNs) for the IAM role that is assigned to the EC2 instances included in the KOTS cluster.
To save tenant assets:
Create a new security group for the EFS that allows inbound access for the TCP protocol on the NFS port (2049) from all EC2 instances that are included in the KOTS cluster.
Select a security group that is assigned to the EC2 instances as the source.
Confirm that the EC2 instances included in the KOTS cluster have a security group that allows outbound access on the NFS port to the security group created in the previous step.
Create the Amazon EFS file system:
From the Amazon EFS Management Console, select Create file system.
In the Create file system page, select Customize.
On the File systems setting page, configure the following, then select Next:
Name — Enter a name that allows you to easily identify the EFS.
Availability and Durability — Regional.
Automatic backups — Enable automatic backups during off hours to avoid backup inconsistencies.
Performance mode — General Purpose.
Throughput mode — Bursting.
Encryption — Enable encryption of data at rest.
On the Network access page, configure the following, then select Next:
Virtual Private Cloud (VPC) — Enter the name of the VPC where the KOTS cluster is running.
Mount targets — Verify that a mount target is created per Availability Zone, then assign the security group you created earlier.
Using the template below, generate a file system policy for the EFS, replacing the <arn-cluster-role> parameter with the ARN of the cluster role. Then, attach the policy to the EFS.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Deny", "Principal": { "AWS": "*" }, "Action": "*", "Condition": { "Bool": { "aws:SecureTransport": "false" } } }, { "Effect": "Allow", "Principal": { "AWS": "<arn-cluster-role>" }, "Action": [ "elasticfilesystem:ClientRootAccess", "elasticfilesystem:ClientWrite", "elasticfilesystem:ClientMount" ] } ] }On the Review and create page that opens, review the file system configuration groups, then select Create to create your file system and return to the File systems page.
Edit the cluster role:
Generate the ARN of the newly created EFS, replacing <region>, <account-id>, and <file-system-id> parameters:
arn:aws:elasticfilesystem:<region>:<account-id>:file-system/<file-system-id>
Generate the ARN for the access points, replacing <region> and <account-id> parameters:
arn:aws:elasticfilesystem:<region>:<account-id>:access-point/*
Important
The template must be used as is, with the policy targeting all access points.
Use the following template to create a new IAM policy, replacing the <arn-efs> with the ARN generated in step 3a and replacing the <arn-access-points> parameters with the ARN generated in step 3b. Then, attach the new policy to the cluster role.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "ec2:DescribeAvailabilityZones" ], "Resource": "*" }, { "Effect": "Allow", "Action": [ "elasticfilesystem:DescribeAccessPoints", "elasticfilesystem:DescribeFileSystems", "elasticfilesystem:DescribeMountTargets" ], "Resource": "<arn-efs>" }, { "Effect": "Allow", "Action": "elasticfilesystem:CreateAccessPoint", "Resource": "<arn-efs>", "Condition": { "StringLike": { "aws:RequestTag/efs.csi.aws.com/cluster": "true" } } }, { "Effect": "Allow", "Action": "elasticfilesystem:DeleteAccessPoint", "Resource": "<arn-access-points>", "Condition": { "StringEquals": { "aws:ResourceTag/efs.csi.aws.com/cluster": "true" } } } ] }
Install the AWS EFS driver version 1.3.8 in your cluster:
kubectl apply -k "github.com/kubernetes-sigs/aws-efs-csi-driver/deploy/kubernetes/\ overlays/stable/?ref=tags/v1.3.8"
The following containerd images are downloaded to your EFS driver: amazon/aws-efs-csi-driver, public.ecr.aws/eks-distro/kubernetes-csi/node-driver-registrar, public.ecr.aws/eks-distro/kubernetes-csi/livenessprobe.
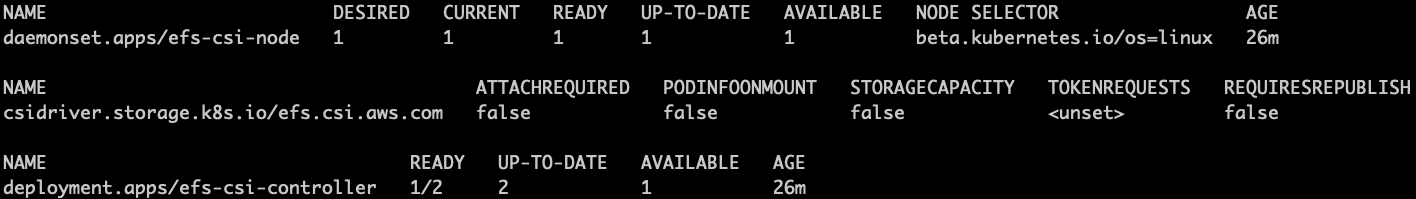
Verify that the driver was successfully installed:
kubectl get daemonset.apps/efs-csi-node csidriver/efs.csi.aws.com deployments/\ efs-csi-controller -n kube-system
Enable the EFS Storage Class.
Log in to the KOTS Admin Console, select the Config tab, then scroll to the AWS Resources section.
Select Enable EFS Storage Class.
In the AWS EFS Storage Class section under File System ID, enter the ID of the newly created EFS.
Remove existing PVC and assets.
Important
If Jama Connect has been deployed and you want to move your assets to EFS, you must first back up tenant assets to a TAR in KOTS.
From the primary node, delete the StatefulSets of the core pods:
kubectl delete sts/core sts/core-ingress sts/core-reports sts/core-jobs
Delete the PVC that contains the assets, so that a new PVC can be created that points to EFS:
kubectl delete pvc/tenantfs
Save assets in EFS.
From the KOTS Admin Console, scroll to the Storage section, then in the Assets Storage Class field, enter the name assigned to the EFS Storage Class.
Save your changes and deploy Jama Connect.
(Optional) Once the core pods are running, restore tenant assets from a TAR in KOTS.
Run this command:
kubectl get pvc/tenantfs
The output displays storage class as the name assigned to the EFS storage class.