Configure SAML authentication
To configure SAML authentication, you must first update the authentication properties.
Important considerations
To connect multiple instances of Jama Connect to the SAML service, you must create unique metadata or applications for each instance through the identity provider. This is true for any combination of production, sandboxes, or self-hosted instances. The entity ID is a unique value that allows the service and identity provider to locate each other and send users to the correct Jama Connect instance.
We recommend testing an integration instance before using SAML on a production instance. For example, disable a sandbox instance from SAML before connecting on a production instance.
Starting with Jama Connect 8.48, organizations that use SAML can use electronic signatures, which are enabled by default. If your identity provider (IdP) can't process the re-authentication, you can disable signatures.
You can enable a different authentication method at any time. If you do, SAML is disabled.
You can control the auto-provisioning of new SAML users in both single SAML and multi-mode. If your users are set up in SAML but not yet added to your Jama user table, this option allows you to control whether users can auto-provision in Jama Connect.
When this option is selected and properties are saved, your SAML users (SAML and multi-mode) can’t sign in to Jama Connect until you add them to the Jama user table. A message tells them to finish the authentication process with their administrator.
This option is selected by default after you upgrade to 8.62.
To configure SAML authentication:
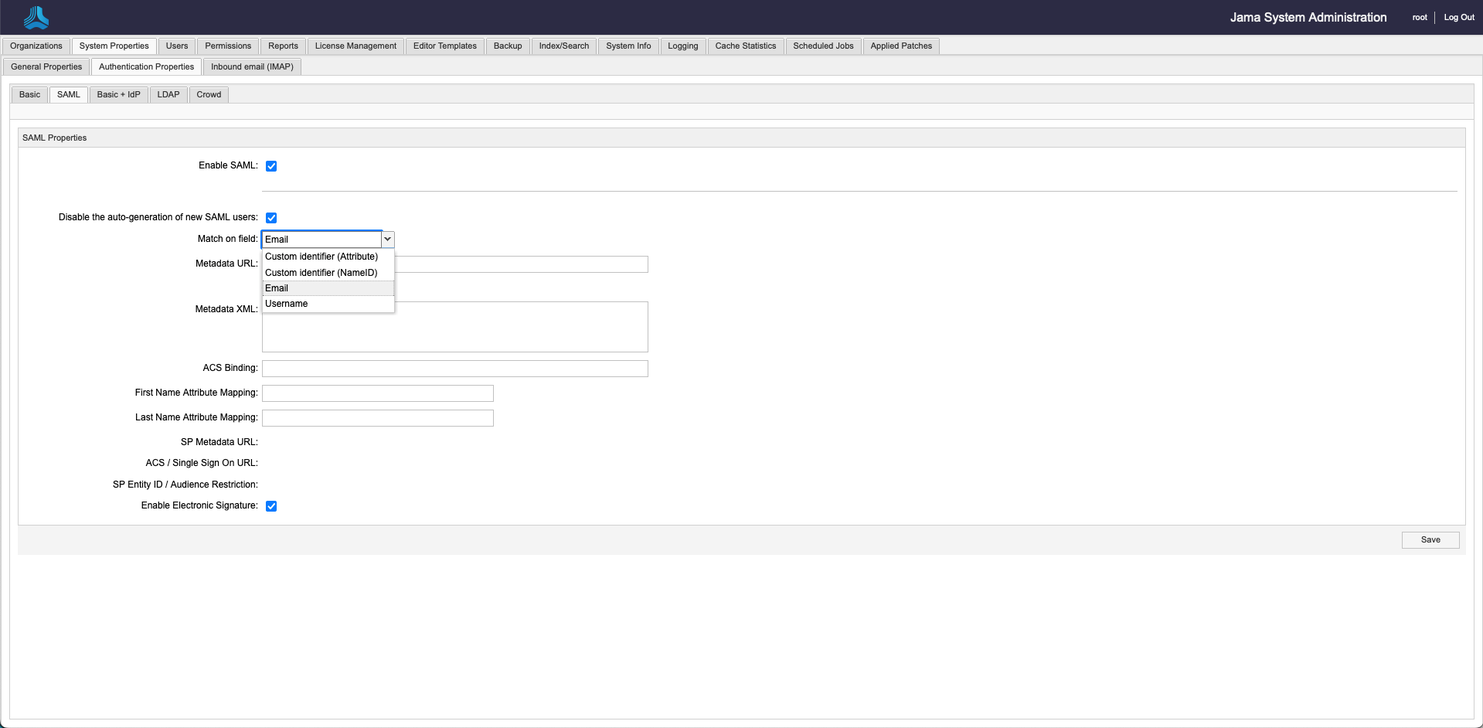
Select System Properties > Authentication Properties > SAML.
Before you enter data, select Enable SAML, then select Save.
Note
The following selections for the Match on field configuration are beta features that are under development: Username, Custom identifier (NameID), and Custom identifier (Attribute). For now, use the default Email selection. If you're interested in beta testing the Username or Custom identifier selections, contact your account manager.
Contact your identity provider for the metadata URL or XML, then paste it in the appropriate field.
If a connection is established, the last three read-only fields are auto-populated with a URL.
SP metadata URL — https://saml-or.jamacloud.com/saml/metadata/alias/defaultAlias
ACS / single-sign-on URL — https://saml-or.jamacloud.com/saml/SSO/alias/defaultAlias
SP entity ID / Audience restriction — https://saml-or.jamacloud.com/saml/metadata/alias/defaultAlias
If the connection doesn't work, you might need to adjust the information in the ACS binding, First name attribute mapping, and Last name attribute mapping fields or contact support.
Tip
The mapping fields serve as the key that connects user identity between Jama Connect and your identity provider. If name attribute mapping fields aren't specified, then a new user's full name defaults to their email address.
Select Save.
Once SAML is enabled, Jama Connect redirects all users to the identity provider's login page. The Jama Connect login page is only accessible for system administrators if they log in as the root user with this URL:
https://your-jama-url/casper/login.req